The Apiculture challenges are dedicated to API attacks. It is basically a honey’s addict website:
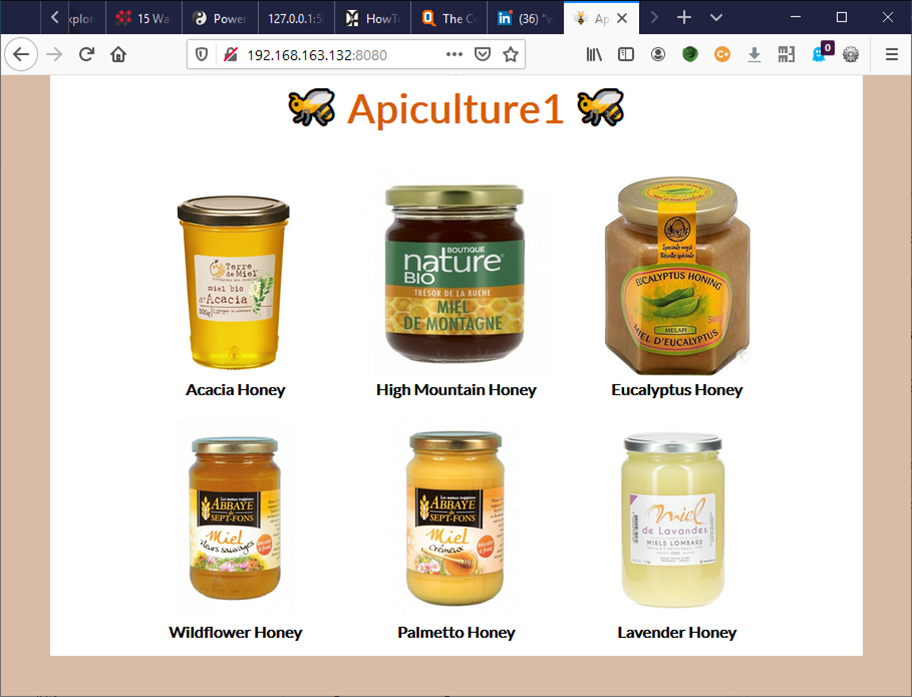
To solve the first challenge, we should pay attention to the call to the /api/products/ API:
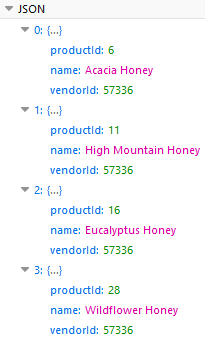
This endpoint provides information to the Angular front-end so that the page can be rendered in the browser… But it is impacted by an Improper Data Filtering vulnerability, since it reveals data [i.e. the vendorID field] that is not used in the webpage. We can indeed discover that all products have been published by the same vendor, whose ID is 57336:
We should then try to discover other endpoints. Fortunately for us, the developer kept a detailed description of his APIs at /api/swagger.json:
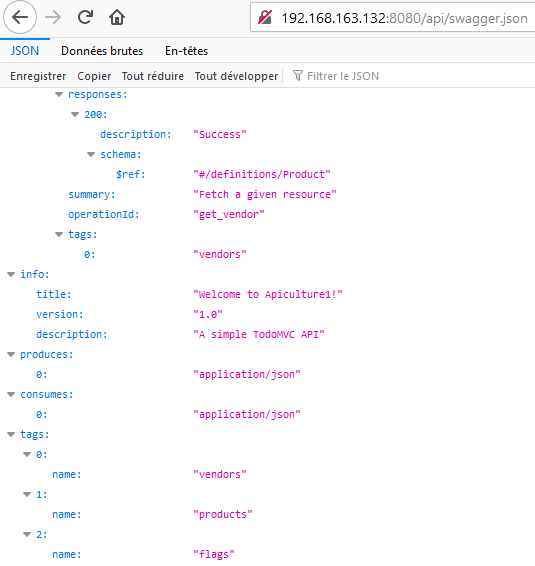
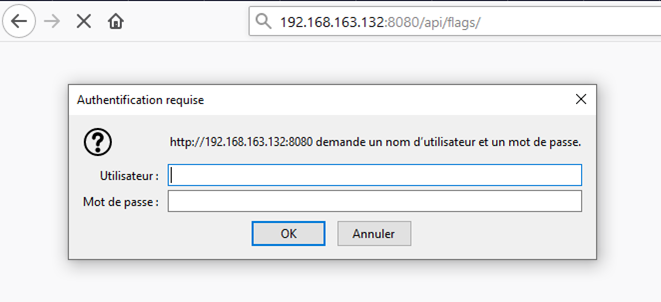
The /api/flags/ endpoint sounds particularly interesting… But it is protected by a Basic Auth:
Let’s have a look to the /api/vendors/ endpoint. It reveals interesting information when we provide the vendorID that leaked through the initial Improper Data Filtering vulnerability:
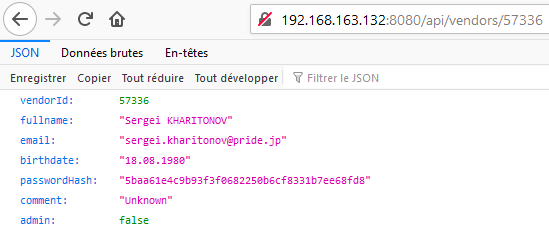
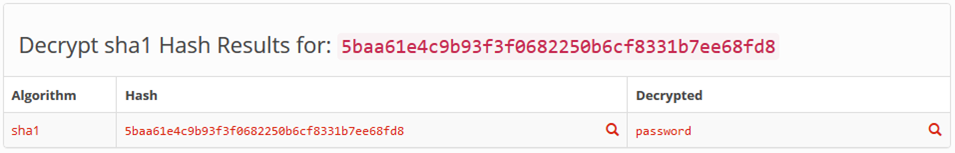
So, we know that the vendor is a simple user and we have his password hash. This SHA1 hash can cracked quickly or simply googled to get the weak password of this vendor:
Nevertheless, it doesn’t permit to access the restricted /api/flags/ endpoint… But we can exploit an Insecure Direct Object Reference vulnerability to get information on other vendors:
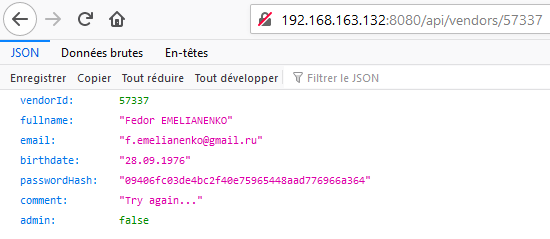
After a few attempts, we discover that the vendor 57332 is an administrator:
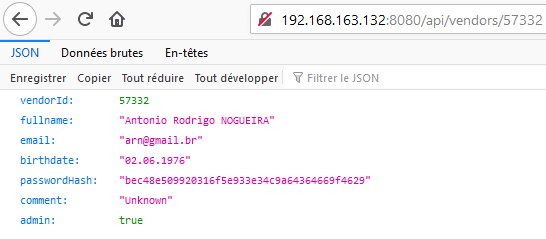
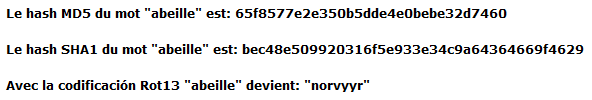
And his weak password can also be googled easily:
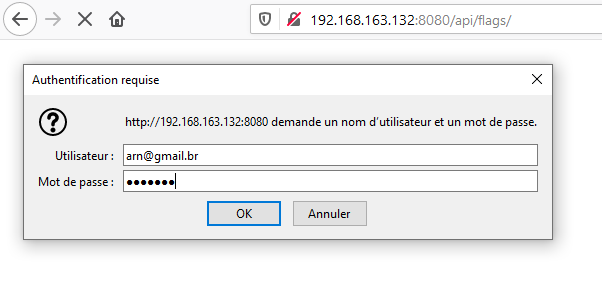
We can now log as Antonio Rodrigo NOGUEIRA with the arn@gmail.br user and the abeille password:
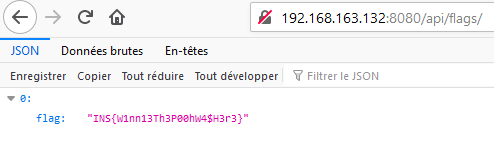
And finally enjoy our flag:
Thanks for playing with Apiculture 1,
Frédéric BOURLA & Simon DENEL
