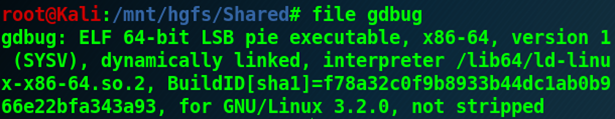
The GDBug file is an ELF binary:
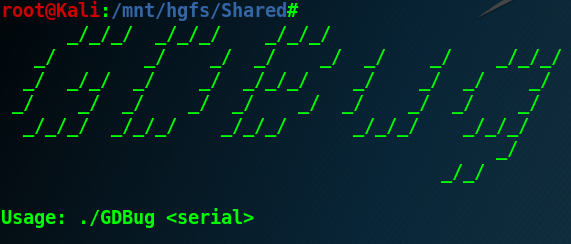
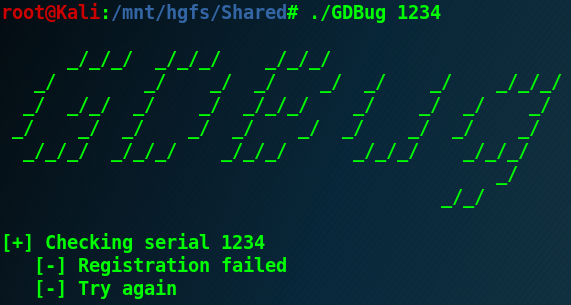
It simply requires a valid serial that we should identify:
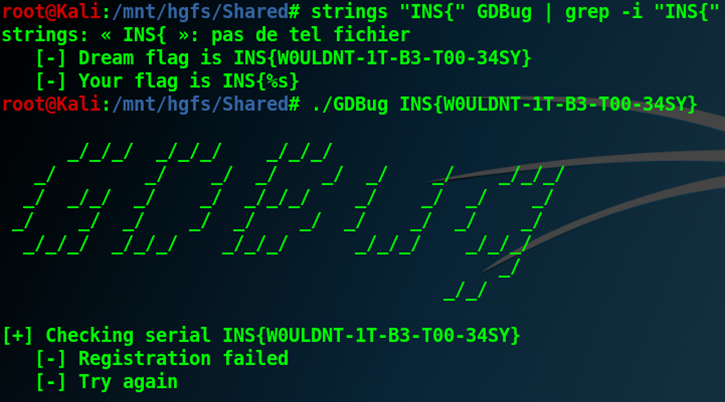
The strings do not reveal anything, besides a fake flag which is not accepted:
Anyway, the binary doesn’t seem to have particular protections:
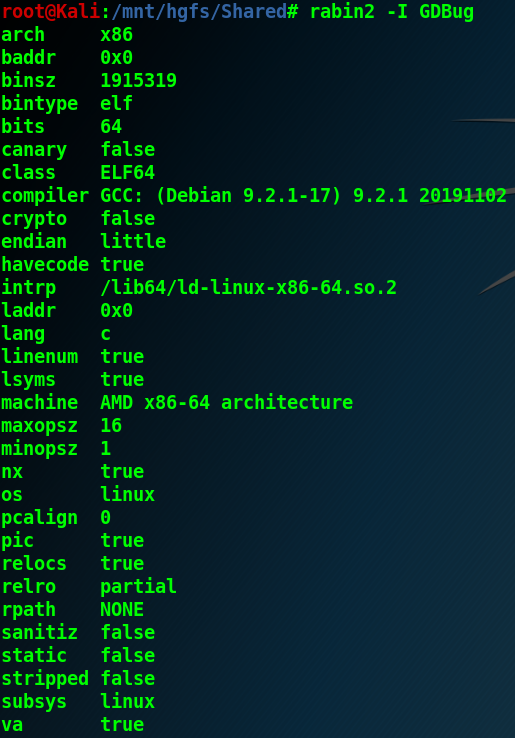
There only seems to be a basic anti-debug:
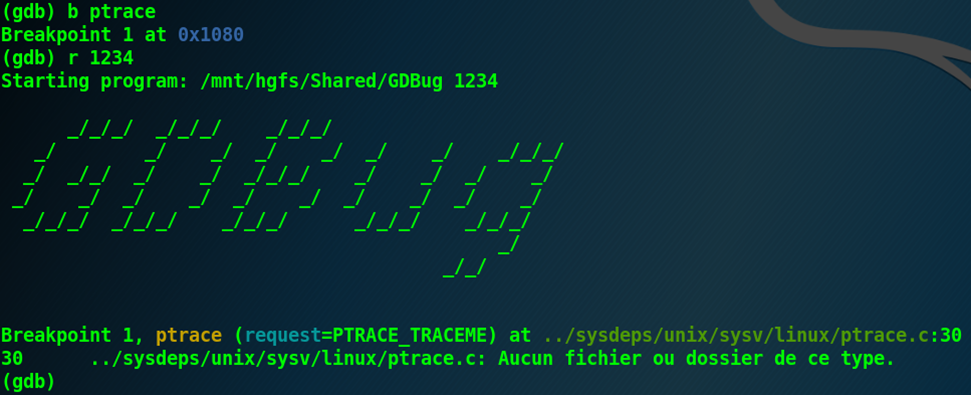
But old versions of GDB and Radare2 have difficulties to analyse the binary:
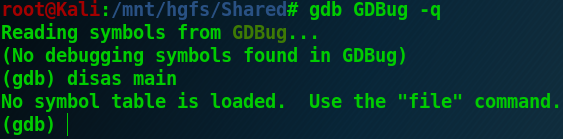
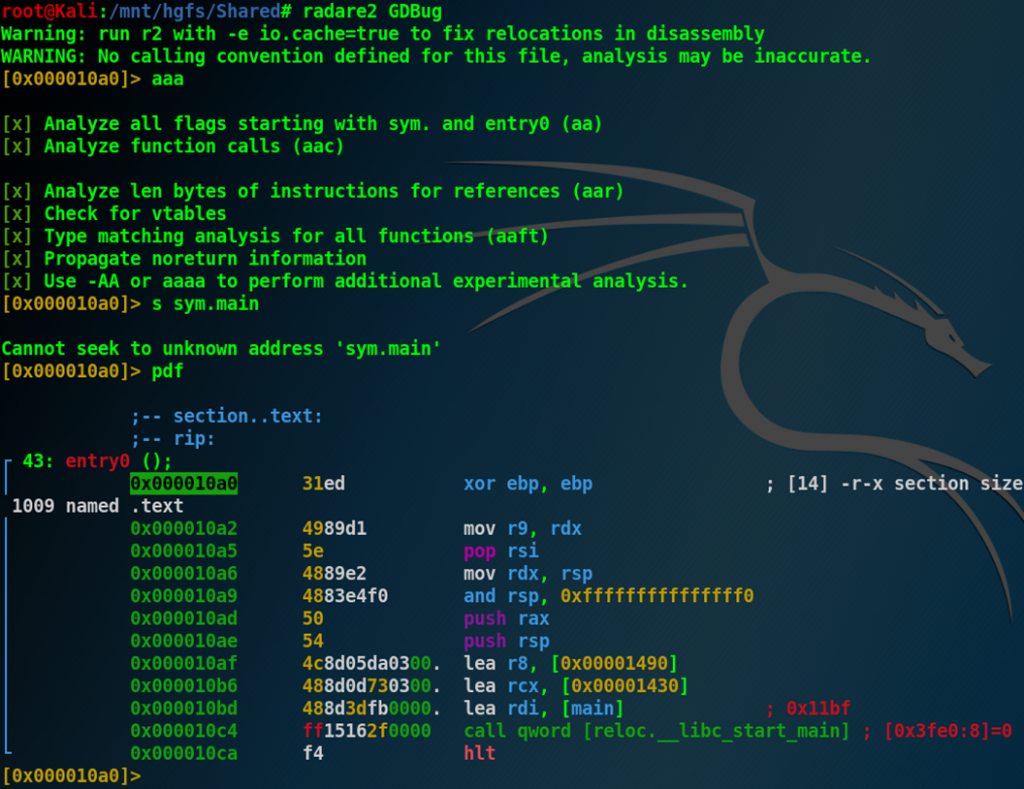
It was indeed supposed to be tricky since the binary was glitched in a way to disturb disassembly within GDB and Radare2… But the problem is that this challenge has been written 3 years ago, in the good old pre-covid time. Nowadays the PE can be parsed without any issue, it is very easy to disassemble it and even to decompile it… For example with Ghidra:
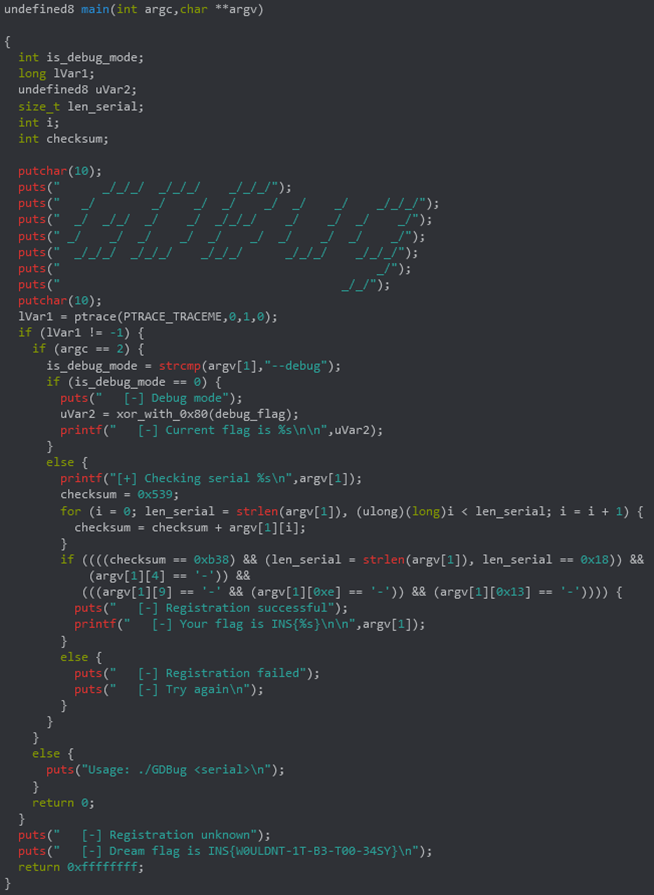
The biggest difficulty having disappeared, it is today very easy to get working serial numbers if we pay attention to generate a 24-chars long string which has a dash on 4th, 9th, 14th and 19th position, and whose sum of all ASCII characters equals 1535.
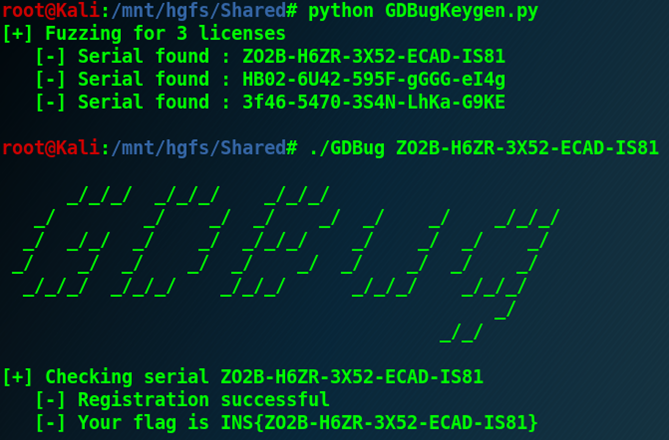
That’s it. Sorry if it was too easy, and even more sorry for those who didn’t see on Discord that many serials would be accepted. Next chall will be harder, I promise. :-]
Frédéric BOURLA
