As most people, we have been waiting for the release of the technical details surrounding the WPA2 vulnerabilities discovered by Mathy Vanhoef (@vanhoefm).
While the details and the full paper (https://papers.mathyvanhoef.com/ccs2017.pdf) are now available, here is a summary aimed at providing the big picture as well as a few recommendations about this attack.
Note that we could at this stage not experiment ourselves with this attack (no PoC or exploit tool is publicly available yet) so this article is solely based on the information published by Mathy Vanhoef and on common knowledge about WiFi and WPA2 (aka Wikipedia).
WPA2
WPA2 is currently the standard security protocol used to protect WiFi networks. It replaces WPA (which was used a temporary standard) which in turn was meant to replace the original (and very weak) WEP protocol. Since March 2006, all devices bearing the WiFi logo must be WPA2-certified.
WPA2 comes in two different flavours, usually referred to as WPA2-PSK and WPA-Entreprise and that differ by their authentication details and, consequently, by the details of the Master Key (called Pairwise Master Key) derivation mechanism. While WPA2-PSK derives this key from a shared secret (called Pre-Shared Key), WPA-Entreprise derives it from an underlying authentication mechanism.
However, whatever the authentication and PMK derivation details, both flavours of WPA2 then use this master key to derive sessions keys (called Pairwise Transient Key) that are ultimately used to encrypt data over the air. This encryption also comes in various flavours which are :
-
TKIP
A deprecated encryption mechanism based on RC4 and meant to be retro-compatible with hardware initially designed for WEP encryption; -
CCMP
The currently recommended encryption protocol, based on AES (in CTR mode) and CBC-MAC authentication code; -
GCMP
A new mechanism (also based on AES but operating in Galois/Counter Mode) that is used by the 802.11ad variant of WiFi (branded WiGig). This protocol seems to be still mostly unknown today (to be honest I had never heard about it before reading Mathy’s paper) but is apparently meant to become very widespread in the future.
In order to encrypt the data that is sent over the network, these encryption algorithms operate as stream-ciphers (RC4 actually is a stream-cipher, AES is called a block-cipher but both CTR and GCM modes of operation are meant to allow it’s used as a stream-cipher). Stream-ciphers produce a continuous key-stream that is used to encrypt data (e.g. by XORing the two). This can result (depending on the cipher itself) on a very strong encryption mechanisms as long as some constraints are respected (e.g. having a strong randomness source for (random) elements used to generate the key-stream and never to re-use the same key-stream).
KRACK attacks in a nutshell
When a device connects to a (non-open) WiFi network, it establishes a dialog with (one of) the access point(s) that is meant to authenticate the device (prove that it has the Pre Shared Key or valid authentication credentials depending on the “flavour” used) and that ultimately leads to the establishment of a session key (PTK) that is used to encrypt the data over the network. This dialog is part of the WPA2 standard and is called “4-way handshake”. This “handshake” is not only used upon initial connection but it is also performed again afterwards, on a regular basis (e.g. every hour) to refresh the session key (agree on a new key).
As the name suggests, this exchange is based on 4 messages, carrying, among other things, a pair of nonces (“numbers used once”) – one chosen by the client (called supplicant in the standard) and the other by the access point (called authenticator) that have a direct impact on the key-stream that is generated by the ciphers.
An overview of the WPA2 4-way handshake is reproduced below (source: https://papers.mathyvanhoef.com/ccs2017.pdf)
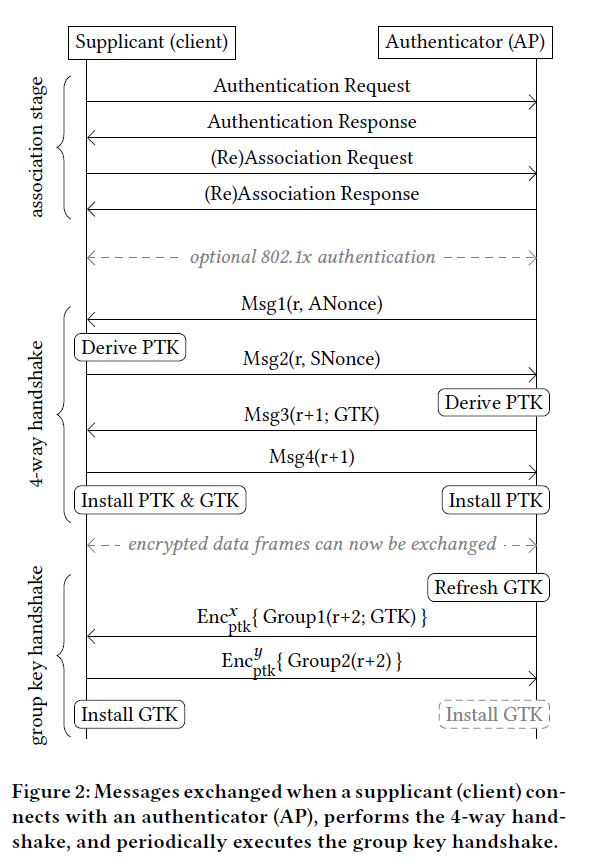
Now … In very simple terms (much more technical details are available in Mathy Vanhoef’s paper ) Key Reinstallation Attacks leverage the fact that – because of a design flaw in the WPA2 protocol – if an attacker replays Msg3 of the handshake above, the (target) device will usually treat this replayed packet as if it had not already been received before and will used it to derive (again) the session key (remember that this message contains one of the nonces used to generate the key-stream).
This issue is partly due to the fact that – because it is a wireless protocol – WiFi (and thus WPA2) has to be designed to account for the possibility of having lost packets (interference, jamming, low signal, …). However the problem lies in the details of how this re-transmitted message is then used by the device (e.g. accepting to re-install a key that had already been used in the past).
In very simple terms, the attack is as follows : the attacker waits for the client device to receive Msg3, process it (thus establishing the session key) and respond with the last message of the exchange (Msg4). The attacker then blocks this message (more details below) thus preventing the access point from receiving it. After a timeout, having received no response to its previous Msg3, the access-point will re-send Msg3 again which will cause the client to re-process it and derive (again) the session key, re-setting the nonces (and various internal counters) to previously used values.
In the meantime (between the moment when Msg4 hs been sent by the client, and the new Msg3 is received) if the client has already used the session key to encrypt and send data on the network this will result in the same key-stream being used twice to encrypt data which is a major violation of the proper use conditions of a stream-cipher.
By using this the attacker can (under some additional constraints) decrypt the contents of the affected data packets.
What does the attacker need ?
In order to carry this attack, the attacker must be capable of, not only sniffing the (encrypted) data that travels over the air (that is always granted) but also to block and replay data packets that are exchanged between the client and the access point.
For that, Mathy Vanhoef relies on a technique called channel-based Man-in-the-Middle attack. Basically, the attacker creates a rogue access-point, with the same characteristics (including the AP’s MAC address) but on a different channel (frequency) and tricks the client in connecting to it instead of the legitimate AP. As a result of that, the client and the AP are on different frequencies and don’t “see” each other. The attacker then relays the messages between the two channels with the capability of blocking, delaying or replaying them as wanted.
What are the consequences ?
As the discovered flaws are inherent to the WPA2 standard, one could think that the attack and the consequences do not depend on the device’s manufacturer and/or software… However the reality seems to be quite different. Actually, many different behaviours are described by Mathy Vanhoef, depending on the device details (including some systems being less affected by the attacks because they are in actual violation of the standard).
But roughly speaking, the attacker will be able to perform one or several of the actions below (depending on the targeted devices and software) :
- Decrypt the data packets sent over the network thus having access to the data sent by sent by the targets. Note that this data may still be encrypted by another mechanism (e.g. if the target is browsing an HTTPS website) however any clear-text traffic (e.g. HTTP) would be compromised;
- Replay packets that have been previously sent by the targets;
- Forge new packets and send (“inject”) them on the network. This could be used, for instance to inject malicious content in browsed webpages or replace downloaded files.
On the other hand, note that the attacker will NOT be able to (at least based on the information available so far) gain full access to your WiFi network (i.e. this attack does not allow to recover your WiFi’s password). This attacks thus does not have the same consequences as what has been observed in the past with WEP et even WPS (used to gain access to WPA2 networks).
The special case of Android…
The use of WPA(2) on most Linux systems relies on the use of a program called wpa_supplicant, that implements all the magic related to authenticating and connecting to WiFi networks.
During his research, Mathy Vanhoef discovered that a series of versions of wpa_supplicant – (2.3 to 2.6) in addition to being vulnerable to the key reinstallation attacks – suffered from an additional implementation flaw that resulted in much more catastrophic consequences for this attack. When targeted with this attacks, these versions of wpa_supplicant do not “simply” re-install the previously used key but they actually end up installing an all-zero key thus resulting in catastrophic consequences (the attacker can basically decrypt all the traffic sent by the device).
Android – being a Linux system – also relies on wpa_supplicant. Consequently, it seems that Android 6.0+ versions are affected by this issue thus exposing millions of devices to the most critical form of this attack.
Note that, from the results observed by Mathy Vanhoef, if you have an iOS device (or a Windows computer by the way) you are – on the other hand – only exposed to a very limited subset of these attacks.
What should we do ?
The affected device manufacturers and software editors have been informed by Mathy Vanhoef several months ago in order to allow for the development of fixes, several of which have already been published. A list of affected vendors (and status information) is available at this URL:
Consequently, you should :
- Don’t panic ! It is not WiFi’s doomsday…
- Update and fix all your WiFi devices for which patches are available (access-points, routers, laptops, smartphones, tablets, “smart”-devices, …) as soon as possible;
- If possible, rely on additional layers of encryption (HTTPS, IPSec, …) on top of your WiFi network (that’s always true and recommended);
- Prefer the use of 4G over WiFi (as long as your devices are not patched). Note however that – in its worst case scenario – this attack does not have more serious considerations to your smartphone/tablet than being connected to any public WiFi network;
What’s next ?
Mathy Vanhoef did not – at this stage – publish an actual exploit tool and some of the attacks require non-trivial conditions to be carried. However it is quite obvious that these attacks will very soon be implemented in existing or new tools and ultimately be easily available.
Moreover it most probable that millions of devices (cheap Android smartphones/tablets, IoT devices, …) will never be updated (because the users will never apply the patches and – most of the time – because such patches will not be available).
Consequently, even if this issue will probably be solved on the long run in many corporate environments (as “easily” as deploying patches on a large scale on often non-centrally managed devices may be…), it may leave many home networks and end-user devices vulnerable for a long time.
More interestingly it may very well open the door for similar attacks on other protocols.
