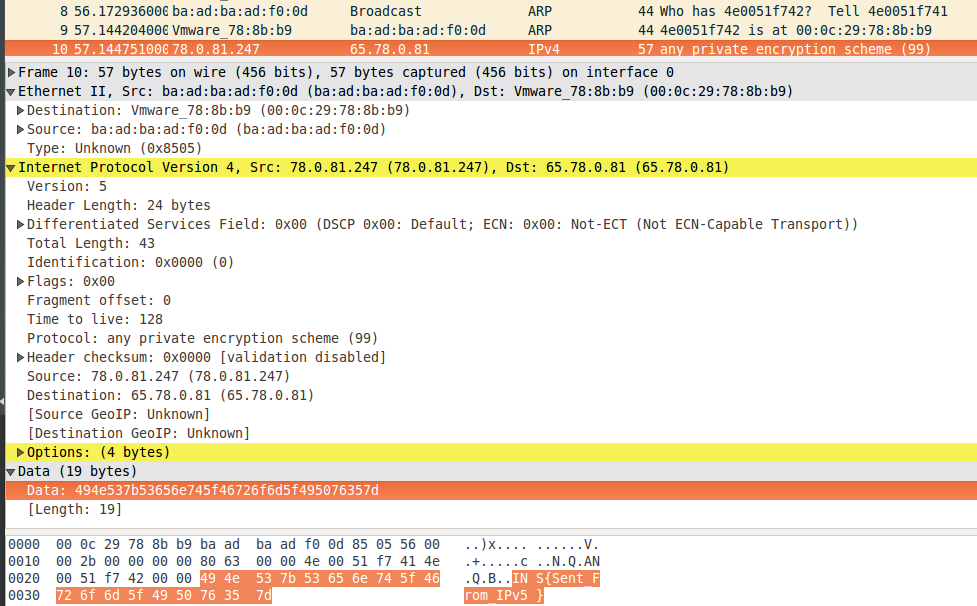
You probably saw on many ‘hackers movies’ weird IP address such a 312.5.125.833. On this challenge, you had to connect on a fake IBM mainframe running on this strange IP stack. After the Z/OS banner, you had to get a shell with “L IMS3270”. No guessing here, it’s simply one of the three suggestions. On the READY prompt, you had a bunch of crappy commands extracted from the Swordfish movie. Only FLAG, IFCONFIG worked. FLAG expects an IP address as parameter. Since this mainframe runs on a non-standard IP stack, you can’t simply enter your IPv4 address. So you have to get a look at the IFCONFIG output:
EZZ2350| MVS TCP/IP NETSTAT CS VM394 EZZ2700| Home address list: EZZ2701| Address Netmask Link Flg EZZ2702| ------- ------- ------- --- EZZ2703| 312.5.125.833 1023.1023.1023.0 CTC1 P EZZ2703| 511.0.0.1 1023.0.0.0 LOOPBACK
We can see a 4x 10 bits netmask.
Trying to use 511.0.0.1 or 312.5.125.833 will send the flag to the loopback address. Useless.
Trying to send to anything other than 312.5.125.x will get rejected with a Network is unreachable. The only thing that seems to do some work is to specify a host in the same net range, but all we get is a “No route to host”.
Somehow the system must translate this IP-like protocol into a link layer address. Let’s start Wireshark and display ARP packets.
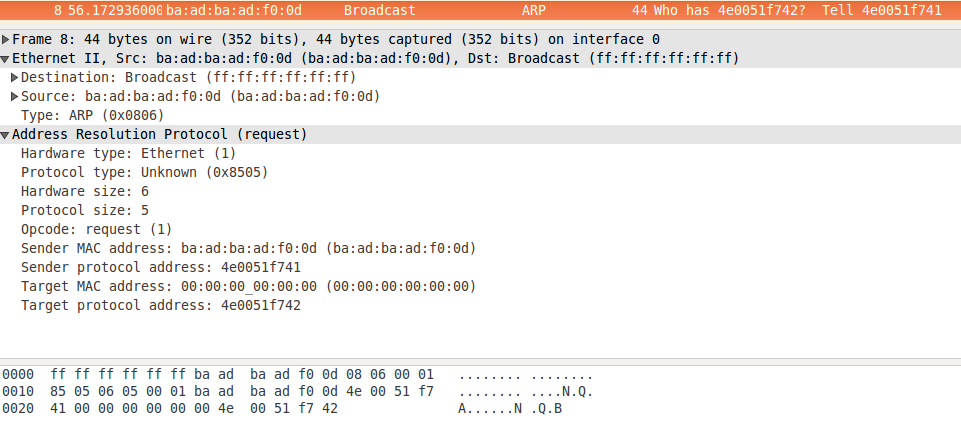
This one looks suspect. Wireshark shows a hex address instead of an IPv4 address. Digging into this ARP packet shows interesting properties:
- Unknown protocol 0x8505 (instead of 0x0800 for IPv4)
- Protocol size: 5 (instead of 4 for IPv4). The size is in byte, so 5 x 8 = 40 bits.
- Protocol address in hex. 4e0051f741 is 312.5.125.833 in 4 x 10 bits big endian. 4e0041f742 is what we entered (here 312.5.125.834)
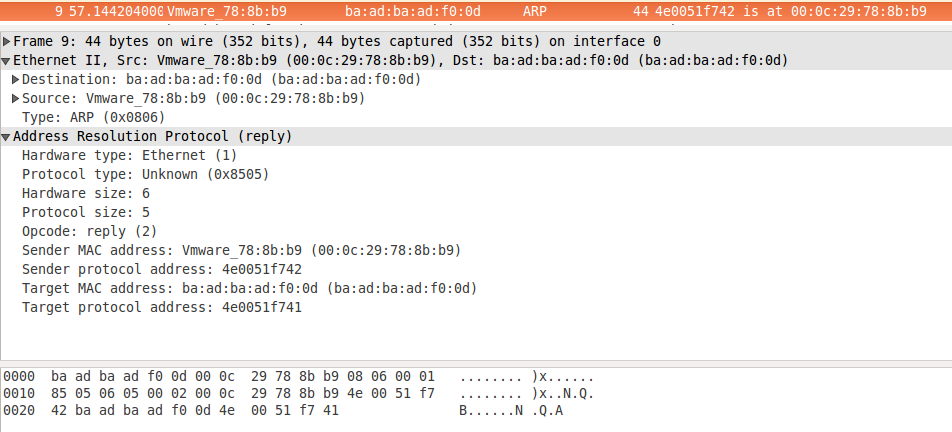
ARP is able to handle oversized IP! What we have to do now is to reply.
We don’t really have to decode the IP like address, or doing any fancy computation. We only have to reuse the incoming ARP packet, set the opcode to 2 (reply) and swap sender/target. Finally we have to fill the sender MAC with our own address.
If successful (and fast enough), the server sends back a packet. If we force Wireshark to decode it as an IPv4 packet, the structure is close enough to be properly decoded. We can find the flag in the data.