As arm CPU are getting more and more used, we decided to create an arm-based wargame consisting of 4 challenges.
The first one, described here, is a reverse engineering challenge that will give you the credentials to access the actual raspberry pi box.
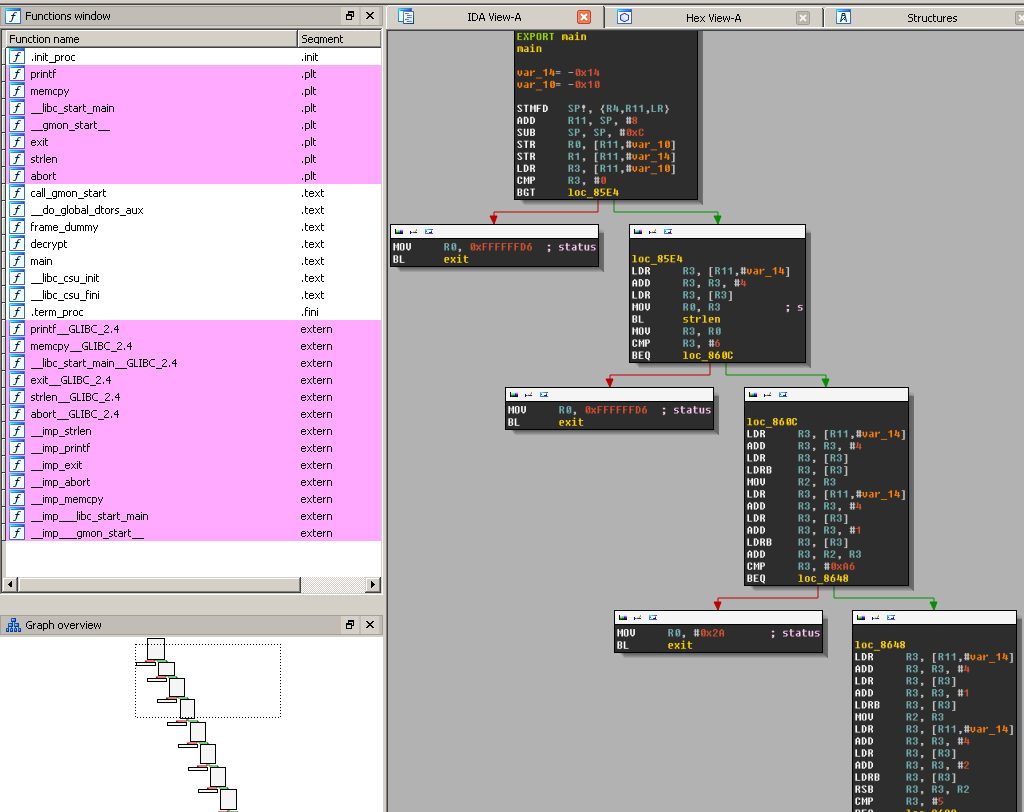
Here is the beginning of the disassembled code:
As you can see, the first check is done again the strlen that must match 6
Then the program parses argv[1][0] and add it to argv[1][1], the result should be 0xa6
Then argv[1][2] is substracted to argv[1][1], the result should be 5.
Here is the c code for all the checks:
[code language=”cpp”]if (strlen(argv[1]) != 6)
exit(-42);
if (argv[1][0]+argv[1][1] != 166)
exit(42);
if (argv[1][1]-argv[1][2] != 5)
exit(-42);
if (argv[1][2]+argv[1][3] != 157)
exit(42);
if (argv[1][3]-argv[1][4] != -66)
exit(-42);
if (argv[1][4]+argv[1][5] != 163)
exit(42);
if (argv[1][5]-strlen(argv[1]) != 43)
exit(-42);
[/code]
So, we can either try to guess the correct sequence or start from the end as strlen(argv[1]) is known. This gives the string
4rm0r1
After that, the real challenge was to be able to run the program without having to reverse the decrypt function 🙂
Any armv6 compatible system could have been used, and we even validated the challenge for the team unable to run the program.
That gave you: # ./armory 4rm0r1Nice, you now have access to the armory!
There are 5 available terminals to get your weapons:
ssh://raspberry1.insomni.hack
ssh://raspberry2.insomni.hack
ssh://raspberry3.insomni.hack
ssh://raspberry4.insomni.hack
ssh://raspberry5.insomni.hack
Login is : level1
Pass is : In33dmoarweap0ns
Be nice, those hosts are based on low cost raspberry Pi !
Use 'who' and try to get one not in use
Be careful with your exploits on this host, don't let someone else steal your flags :-)
Your flag for this challenge:
2ea108cdfa288d2fb66bde68d4f74348bc2799acbdc324ba613368ca1f7fe727168745632e6b6c
972a194dc12589d087cb2819cd46890f7a0527c868b41d6d1a
Now, if you want to be able to run the raspberry pi system in order to try the challenges, there are 3 ways:
- Qemu-user emulation in chroot
- Qemu-system emulation
- On an actual raspberry pi
Qemu-user chroot:
The archive is made for x86_64 systems but it should be easy to make it work on x86 architecture by reading http://www.gentoo.org/proj/en/base/embedded/handbook/?part=1&chap=5
You need the binmft_misc kernel module to make it work. Simply untar the following archive somewhere :
http://www.insomnihack.ch/images/raspberry.tgz
Once untargz’ed go inside the directory and run chroot.sh. If all goes well, you should be chrooted inside a full arm environment and be able to run native arm code on your x86_64 system
Qemu-system with the image:
Download http://www.insomnihack.ch/images/image.img.gz and http://xecdesign.com/downloads/linux-qemu/kernel-qemu
Gunzip the image and launch qemu with :qemu-system-arm -kernel kernel-qemu -cpu arm1176 -m 256 -M versatilepb -append "root=/dev/sda3" -hda image.img -display sdl
You will have some errors about missing kernel module but the console prompt will come eventually.
User is root and password is toor
Native raspberry pi:
Should be pretty straightforward, just download http://www.insomnihack.ch/images/image.img.gz and copy it over a sdcard (in this case /dev/mmcblk0) like this :dd if=image.img of=/dev/mmcblk0 bs=10M
User is root and password is toor
It might take a while to launch the ssh daemon but it is due to the dns name resolution.