What is Splunk ?
Splunk is a Data-to-Everything Platform designed to ingest and analyze all kind of data. They can be visualized and correlated through Splunk searches, alerts, dashboards, and reports. Splunk is the #1 of 2020 Gartner Magic Quadrants in SIEMs for its performant analysis and visionary in Application Performance Management category.
Splunk and SCRT Analytics Team
SCRT provides its Splunk-based SIEM solution focused in first place on suspicious behavior detection through a custom library of use cases based on its on-field experience and know-how in Cyber Security.
SCRT chose Splunk Enterprise and Splunk Enterprise Security providing an integration with customer infrastructure and providing all the Splunk power to ingest, correlate, analyse and display valuable information for anomaly detection.
Nevertheless, Splunk has a lack of a viable solution for a proper whitelisting strategy that would enable users to delete part of their search results. For this purpose, SCRT has developed a custom Splunk app called “Event Masker” that provides filtering functionalities with a simple and powerful whitelist rules editor.
Event Masker
Event Masker provides filtering functionalities in Splunk, thereby permitting you to whitelist the events of your choice. Even though you can use Event Masker on any dashboard or query in the Splunk search bar, it was primarily built to reduce the number of false positives in Splunk Enterprise Security by better controlling its notable events.
Event Masker provides:
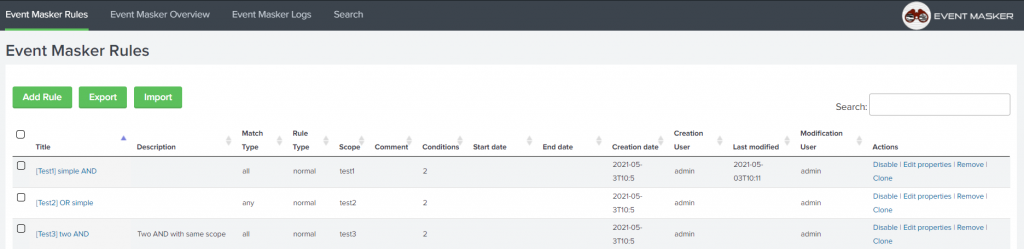
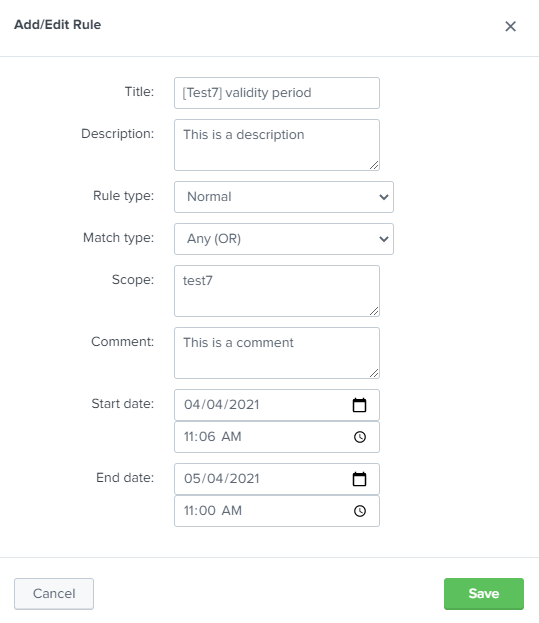
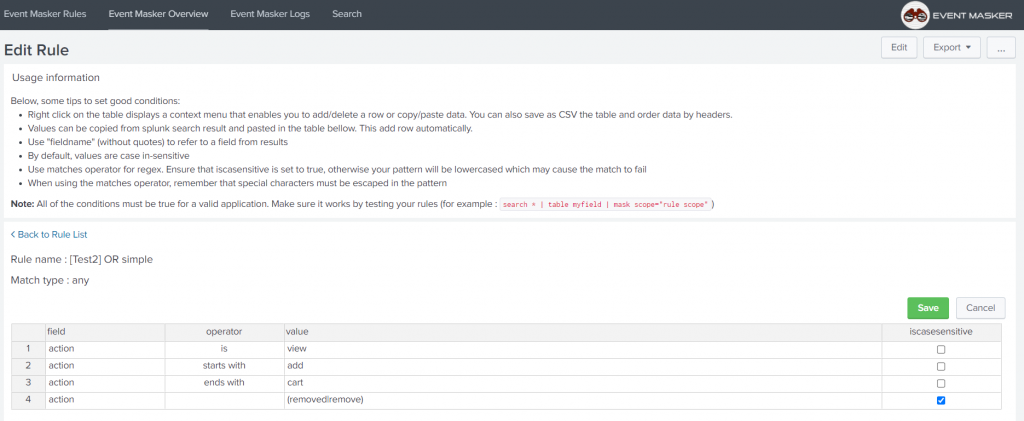
- Rules management through an advanced interface that permits to create, import, export and edit rules properties. Each Rule contains a set of conditions, applied when Event Masker is called in a Splunk search command or correlation search.
- The custom search command “mask” which permits to call Event Masker from the command line.

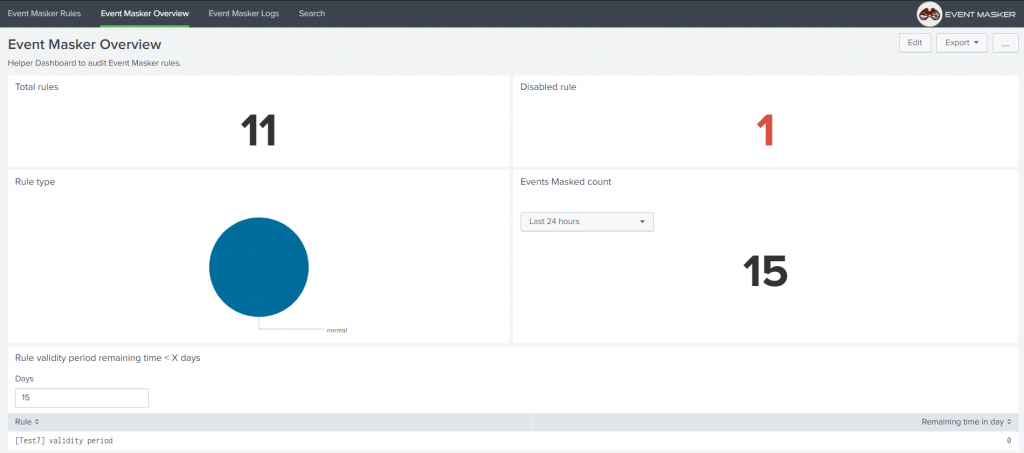
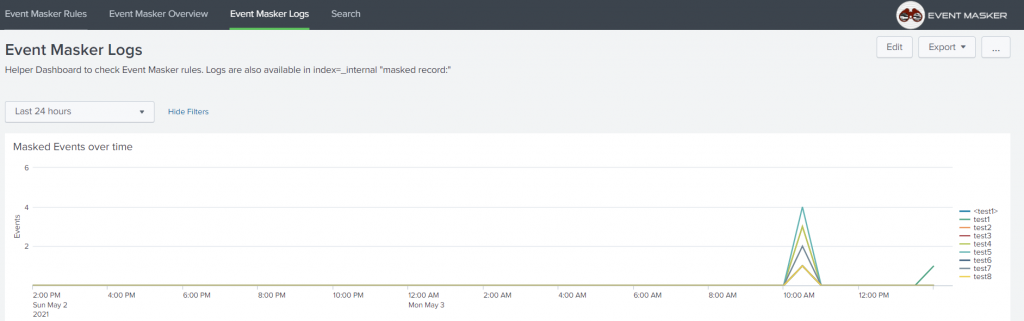
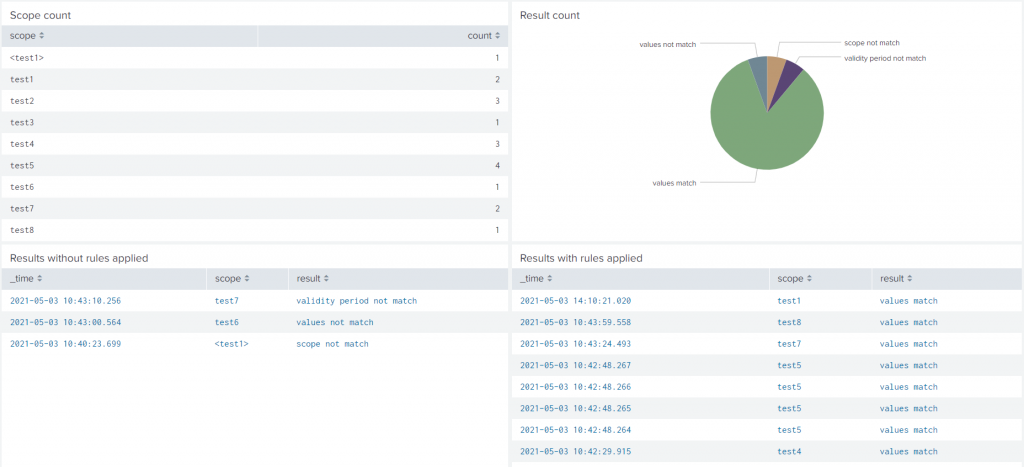
- Some dashboards to audit the masked events and check the underlying rules.An audit log that permits to further track events that were masked over time
Release
Event Masker was released under CC BY-NC 4.0 and published on SplunkBase : https://splunkbase.splunk.com/app/5545/
We are pleased to provide this app freely to the Splunker’s community with a public GitHub repository https://github.com/scrt/event_masker/. Feel free to co-develop with us on this app to improve the Splunk experience and the efficiency of threats detections.
Many thanks to the whole SCRT Analytics team for its expertise and performance that permitted to achieve this great project.
